In the world of cryptocurrency, one of the most pressing concerns is how to balance security with user experience.
How can we keep our customers' keys safe without complicating the user experience?
This is especially challenging for new users who are not yet familiar with the complexities of the crypto world.
Before we dive into this issue, let’s first take a brief look at what public and private keys are. If you’re already familiar with these concepts, feel free to skip ahead.
Blockchain, the technology that underlies most cryptocurrencies, uses a system of pairs of keys: public keys, which are publicly known and are used for identification, and private keys, which are kept secret and are used for authentication and encryption.The private key is what gives a cryptocurrency user ownership of the funds associated with a particular address.
When you use a Blockchain wallet to send cryptocurrency, the software automatically generates and stores private keys for you.
When you sign a transaction with your private key, the network recognizes that you have the authority to transfer the funds associated with the address you’re sending from, without actually disclosing your private key.
Different wallets on the market have varying approaches to securing private keys:
-
Self-Custodial Wallet: The user is responsible for securing their own assets. They are the sole owner of the private key and have full control over their assets. If they lose or have their private key hacked, they lose access to their assets. Usually, the user has to remember a seed phrase.
-
Custodial Wallet: The same platform or a third party is responsible for protecting the private key. The user never has to worry about where they keep their seed phrase or hardware wallet since they don’t have either. Instead, they access their wallet account through a username and password.
-
Shared Custodial Wallet: As the name implies, custody responsibility is shared among several participants to avoid having a single point of failure. There are two different approaches here: multisign and multi-party computation.
Multisignature Wallet: Multiple private keys are connected to the wallet, generating a digital signature that enables two or more participants to sign a transaction as a group.
MPC Wallet: A single private key is connected to the wallet, but a portion of it is encrypted and stored on different devices. Each device, when combined with the others, allows access to the funds.
I will focus on the last scenario, where an MPC wallet can improve security while maintaining a good user experience. This is particularly useful when the user needs to regain access to their funds because they have lost their private key.
What is Multi-Party Computation? Link to heading
Multi-Party Computation (MPC) is a cryptographic protocol that distributes computation across multiple parties, each holding its own private data, where no individual party can see the other parties' data.
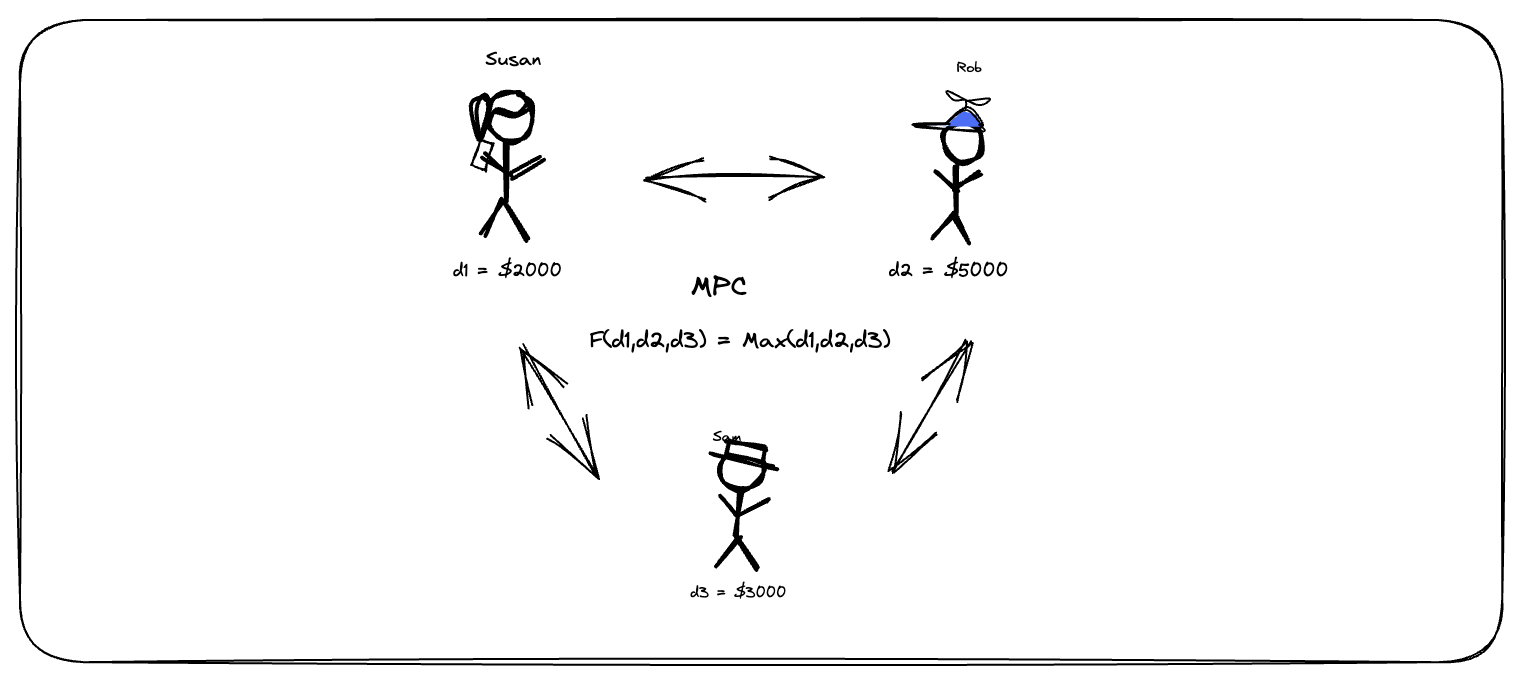
For example, let’s consider three people - Susan, Rob, and Sam - who want to find out who has the highest salary without revealing their salaries to each other. This is a classic example of MPC, known as The Millionaire’s Problem. Using only their own salaries (d1, d2, and d3), they want to determine the highest salary without sharing any actual numbers with each other. Mathematically, this translates to computing:
F(d1, d2, d3) = max(d1, d2, d3)
If there were a trusted third party, such as a mutual friend, they could each tell their salary to that friend and find out which of them makes the most (i.e. F(d1, d2, d3)) without ever revealing their salaries to each other.
The goal of MPC is to design a protocol where Susan, Rob, and Sam can still learn F(d1, d2, d3) without revealing who makes what and without relying on an external third party. By exchanging messages only with each other, they should learn no more than they would have by interacting with their trustworthy mutual friend.
How does this work?
The MPC protocol leverages a well-established cryptographic concept called “additive secret sharing,” which refers to the division of a secret and its distribution among a group of independent, willing participants.
Moving forward in our example, Susan, Rob, and Sam each have a “secret share” that was cryptographically generated between them. Each secret share provides no useful information on its own.
A secret share, after all, is just a piece of incomplete information about the initial secret value from which it was derived.
However, secret shares provide valuable information when added up (hence, the “additive” in additive secret sharing).
In a real scenario, the parties can be the user device, the platform side, and a trustworthy third party.
Three secret shares are generated in each party. That is, there is no single private key stored anywhere. Instead, the private key is “split,” and each party has a portion.
So every time the user wants to move their funds or sign some transaction, a defined threshold of these parties has to coordinate and adhere to.
Some Advantages
- No Single Point of Failure
- Supports Multichain
- Low Gas Fees
- Ease of Administration
- Faster Transactions
If you want to check some implementations of this protocol, take a look at this library made by Binance.